A Tale of Cross Site Request Forgery (CSRF)
What is CSRF ?
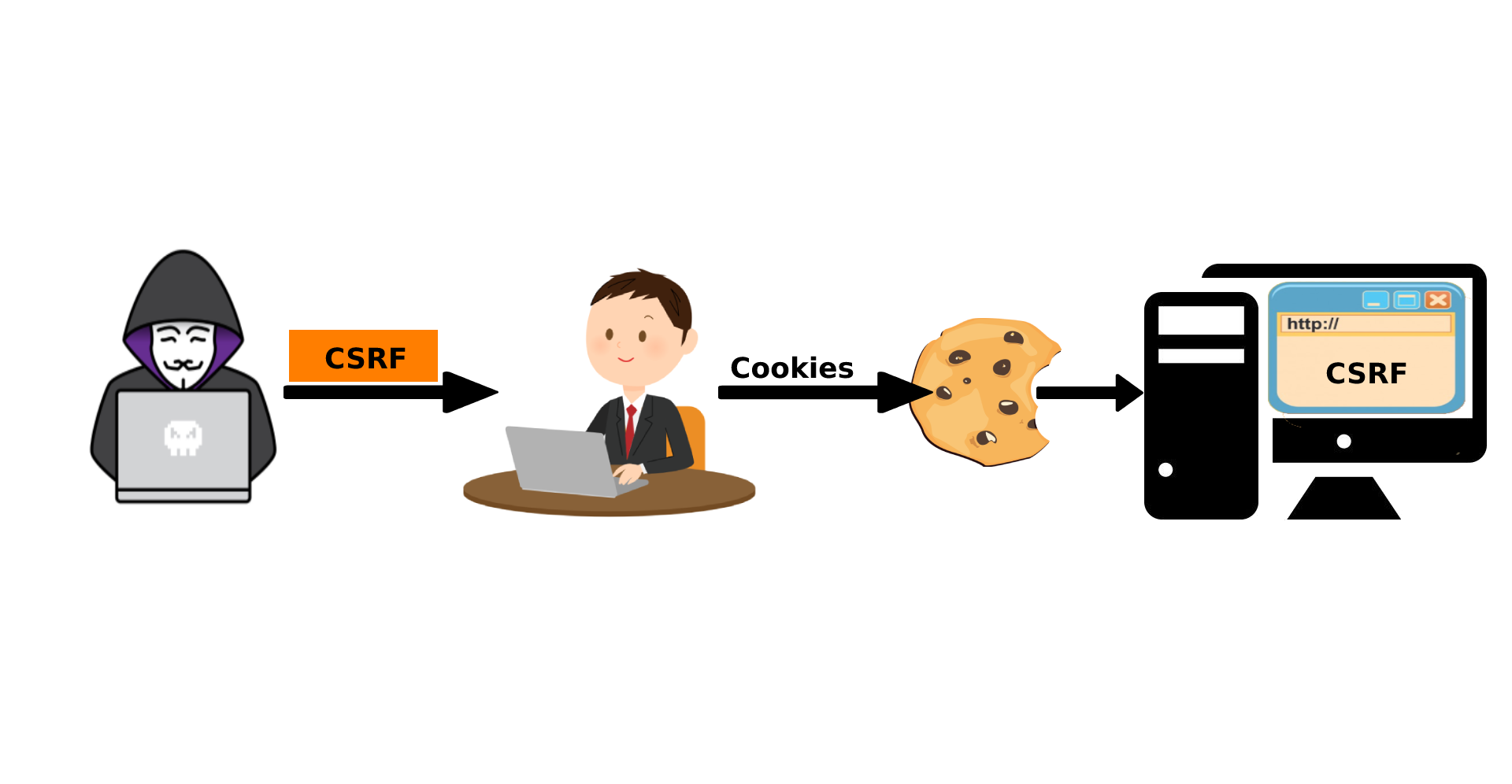
Cross-site request forgery (CSRF) is a common web security vulnerability. It’s also known as XSRF, Sea surf, session riding, Cross-site reference forgery, and Hostile linking. The Successful CSRF vulnerability can have serious consequences that the Open Web Application Security Project (OWASP-2013) has included it in its top 10 vulnerabilities list.
CSRF attack tricks a web browser of an authenticated user to execute an malicious action in an application/web site unintentionally. Web applications can send requests to another web application without showing any response as the user is already logged in, also can only possible when user is logged in and have a valid session cookie.
Example for how the CSRF attack works?
- Login to https://demo.testfire.net/ using default credentials, you will find two accounts.
- Capture the request in any Intercepting proxy (Burp Suite, Charles Proxy etc.) while transferring the amount from one account to another as shown in the below picture.
- Generate CSRF POC using Burp Suite Engagement tools (by modifying the account numbers accordingly)
As the victim is already logged-in to the site an attacker can send the crafted malicious form/URL to the user to his email/text/by any other means and trick the victim using his social engineering skills/techniques like below.
Limited Time Offer Get a $100 Gift Card Now!! (Evil :P)
User thinks, he could use a free $100 gift card! What could go wrong? You open the email and click the link/open the attachment.
Once the user opens the form a transaction is automatically performed from his account without his knowledge as the user is already logged in.
In this case, the attacker tricked user to transfer the money unintentionally.
How CSRF happened:
- User logged into the application, so your browser had your session cookie stored.
- User visited a link that sent through Gmail & controlled by the attacker.
- The attacker sent a request to the server in the exact format that the actual website would’ve used.
- The server receives a completely legitimate request and processes the transaction.
- Then Cross-Site Request Forgery performed.

Anitha Machineni
Security Blogger & Author at Security Souls on Cyber Security