What is XXE?
XXE stands for XML EXTERNAL ENTITY.
Before learning about XXE let’s dive in to know about how the HTML document types are defined and what is DTD.
What is DTD?
DTD is nothing but the abbreviated form of Document Type Definition which defines the structure and the attributes of an XML document. DTD’s can be Internal (if elements are declared within the XML file) or External (if elements are declared outside the XML file) depending on how they are defined.
Every XML document contains a DTD that defines the complete structure of XML.
It can be declared by using the <!DOCTYPE> tag.
For example:
<?xml version=”1.0″ encoding=”UTF-8″?>
<!DOCTYPE INSERT DTD HERE>
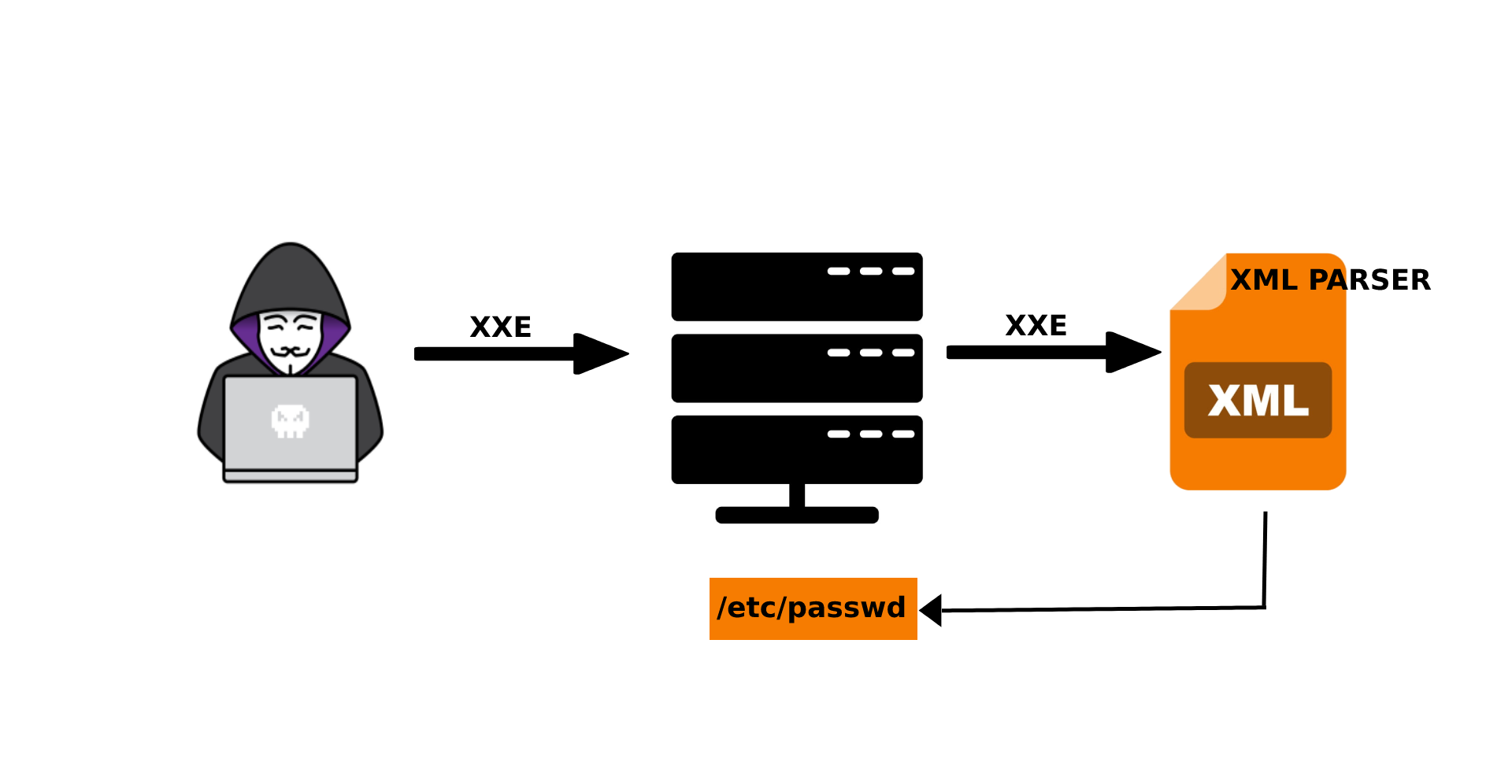
What is XML External Entity Injection?
XML External Entity Injection is defined as vulnerability that allows an attacker to intervene with a web application which parses XML data. It allows an attacker to fetch sensitive files on the application server and use it to access local or remote content.
External DTDs are always identified by the keyword called “SYSTEM” which is used to reference the externally located file on the application server.
<?xml version=”1.0″?>
<!DOCTYPE data [<!ELEMENT data (#ANY)>
<!ENTITY file SYSTEM “file:///etc/passwd“>]>
<data>&file;</data>
How do XXE vulnerabilities occur?
XXE’s arise because of the weakly configured XML Parser. This allows attackers to read sensitive & config files located on the application server.
In the example specified below, the attacker will be able to fetch the “/etc/passwd” file located on the server by using the DOCTYPE element that defines an external entity containing the path to the file.
<?xml version=”1.0″?>
<!DOCTYPE root [<!ENTITY test SYSTEM ‘file:///etc/passwd’>]>
<root>&test;</root>
How to prevent XXE attacks?
The easiest and most effective way to prevent the XXE is to limit the capabilities of a XML Parser.
- When possible, send the data in less complex/lightweight formats like JSON.
- We should upgrade the XML processor and libraries used by the application
- It’s important to disable the External DTD processing in the XML parsers of an application.

Sai Kantipudi
Security Enthusiast, Blogger & Passionate Learner.

